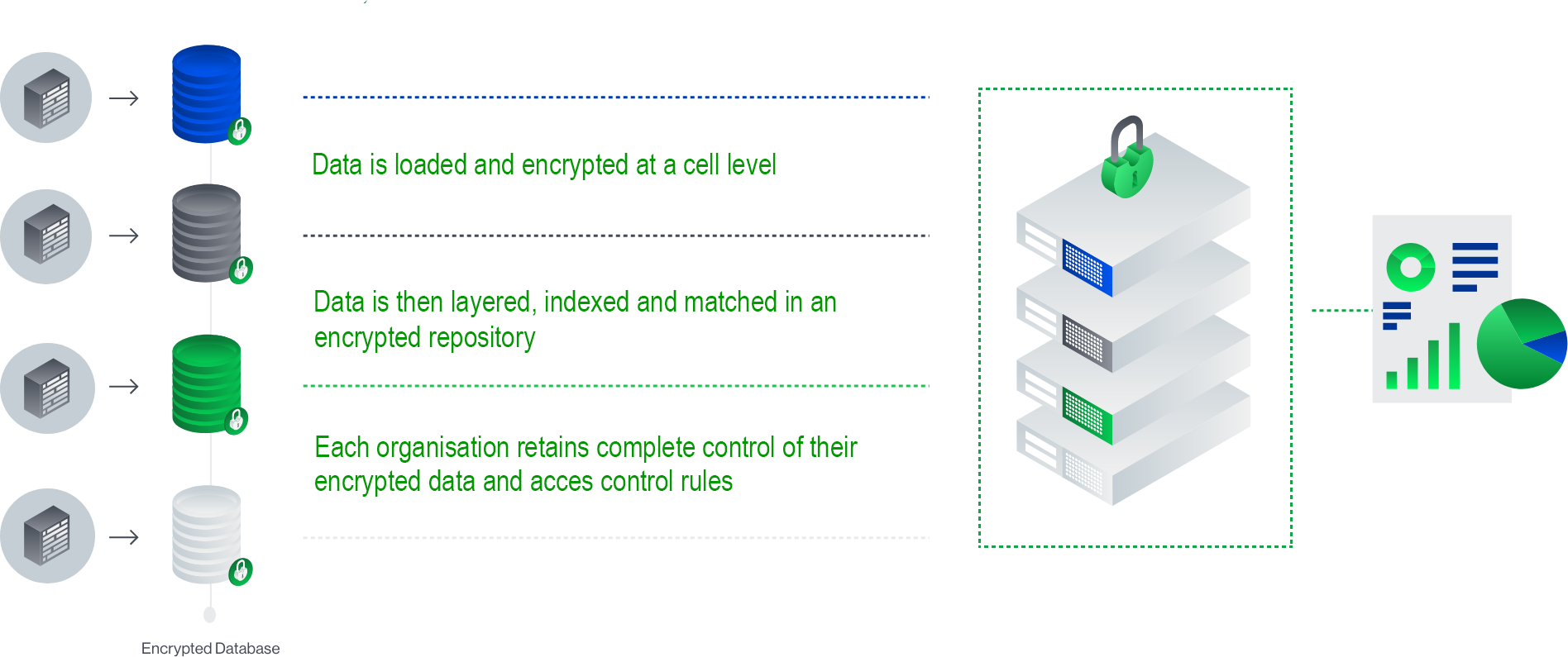
How IXUP works.
Before data even reaches the IXUP platform it is encrypted at source, it is then encrypted during transmission and all matching, processing and computations are performed on encrypted data.
The IXUP platform uses homomorphic encryption at the cellular level, and can run in-depth calculations and analysis on multiple data sets without ever needing to decrypt it.
We follow the National Institute of Standards and Technology (NIST) approved AES-256 encryption protocol.